The federal opposition seems to think it has discovered a “gotcha” to argue against the proliferation of rooftop solar PV – and against Australia’s renewable energy target: Chinese hardware.
Senator James Paterson is leading the charge, fresh from his success in persuading the government to discard Chinese CCTV cameras (here at tech publication iTnews) and calling for the same to happen to 3000+ DJI drones owned by government agencies (disclosure: the author writes for iTnews).
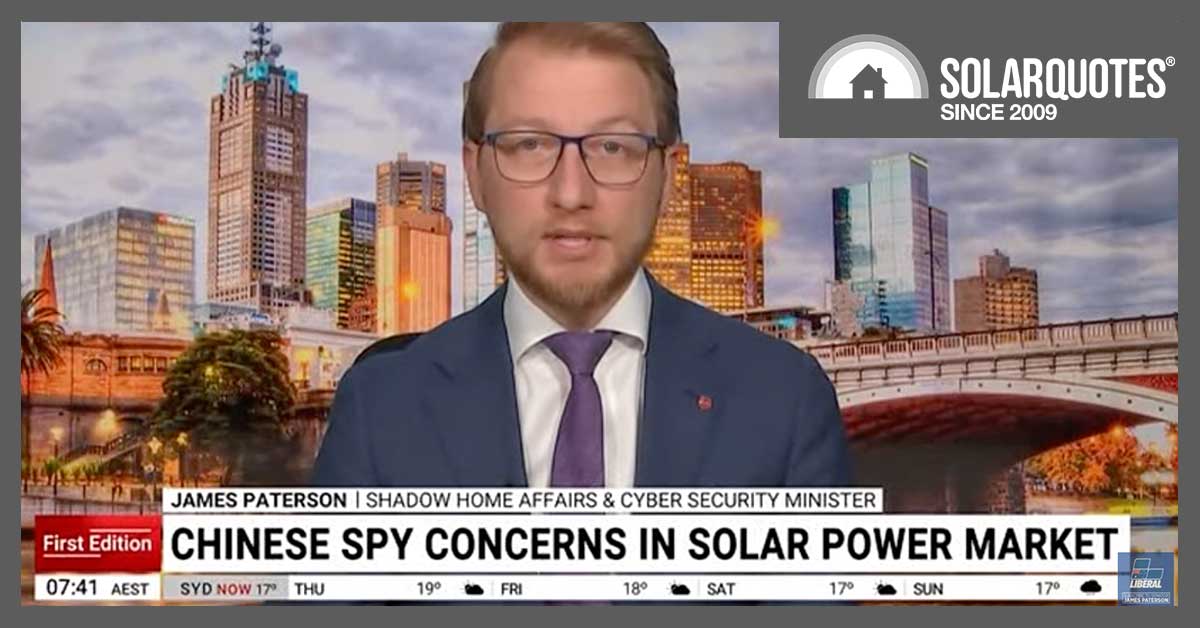
Now, Paterson has the solar business in his sights, taking to News Limited outlets to tell the world that Chinese solar inverters could be used to bring down Australia’s grid.
This Sky News video posted to YouTube says almost all you need to know about the senator’s campaign in the chyron: “Chinese spy concerns in solar power market”.
To quote Senator Paterson from the video:
“These are inverters that are internet-connected, and their role is to connect the solar panels on the roof of your home or business to the grid and make it work.
“The problem that we have is that the smart inverters … are predominantly made by Chinese companies, including companies like Huawei.”
The senator believes there’s a “critical mass” of devices at which they become “a significant proportion of our electricity grid”.
“That could be disrupted by an external party, by a signals intelligence agency like the People’s Liberation Army’s cyberspace force or the Ministry of State Security cyber hacking unit.”
How Great a Risk?
China-baiting has proven fruitful for conservative politicians worldwide ever since they began campaigning against Huawei from supplying major telecommunications projects like 5G networks and the NBN.
In this case, the China-baiting appears to have at its heart the opportunity to attack the government over its ‘82% by 2030’ renewable energy target, because the target will bring more Chinese kit into Australia’s solar PV supply, increasing our exposure to whatever the Chinese Communist Party has in mind.
It’s easy to think that attacking the renewables target, rather than a genuine understanding of the cyber security risks, is the point of the coalition’s campaign.
And it would be a travesty if renewable energy targets became hostage, yet again, to political point-scoring.
So how genuine are the risks?
Regular readers will know that I believe the solar PV industry needs to take cybersecurity seriously and that security vulnerabilities have been found (and fixed) in inverter products.
However, the risk of a critical security vulnerability – such as an unsecured login to an inverter – isn’t dependent on a product’s country of manufacture. Any internet-exposed device with a vulnerability can be exploited by any attacker that finds it.
Senator Paterson appears to be hinting that the Chinese vendors are building secret backdoors into their products – that one day ten thousand Huawei inverters (or Growatt or Solax or Sungrow or any of many) will be taken over by state-backed Chinese hackers to bring down the grid.
At the very least, Senator Paterson is assuming that there is no way to stop this happening.
And that isn’t true.
For one thing, grid-connected, internet-connected inverters don’t exist in a vacuum.
If they’re part of a Virtual Power Plant, they’ll be controlled by a third party who manages the import and export of grid electricity from the battery. If they are part of a Flexible Exports program (currently mandatory in SA and optional in QLD) a third party will control how much solar can be exported to the grid.
These programs are not managed by a consumer who doesn’t understand cyber security – they should be in the hands of organisations with cyber security expertise familiar with the Australian Signals Directorate’s Essential Eight cyber security control list, and its Australian Information Security Manual.
At the very least, organisations controlling fleets of inverters can ensure that smart inverters communicate with the network management centre over an encrypted channel and don’t make connections to or from Chinese network addresses.
And if the organization controlling thousands of inverters through the cloud is one of the big genetailers (AGL, Origin, Energy Australia, etc.), they’ll be in the hands of companies that already invest millions in security and are subject to the Security of Critical Infrastructure Act.
That Act was initiated by the previous government – the one of which Senator Paterson was a part.

 RSS - Posts
RSS - Posts


I’ve watched James Patterson for a while. I like him and think he is one of the better people representing us in Canberra. He doesn’t do “Politics” very well; it is usually obvious when he trots out talking points instead of something he is passionate about.
He does, however, have a bit of a blind spot when it comes to risk from China. He has seen many security assessments, which has made him a little paranoid. I think he has over-egged the risk here.
That’s not to say there is no risk.
Regardless of whether you believe Beijing to be white as the driven snow or a dangerous threat to national security, diversity is a smart move. (Disclosure: I opted for non-Chinese panels+inverter to avoid economic hegemony, not because of hacking concerns).
As for the virtual power plant point, is that actually relevant? If backdoors are built into the inverters, and there have long been reports of computers, motherboards, routers, Android devices, and more being compromised, then MSS or the PLA don’t need to hack a third party’s front door, they can directly communicate with inverters.
Perhaps the ultimate nightmare scenario is an Australian government not doing what Beijing wants, then discovering Beijing controls our power, and through it, many of our other resources. Given how Beijing treats its own citizens do we really want to discover we’ve become a tributary state?
I agree.
I bought remote controlled roller blinds for my windows that came with a small wifi controller so they could be operated from an app on my phone. When I ran some diagnostics on the device I found it was regularly calling a routine on a chinese server.
Full firmware listings and testing should be compulsory for any controller devices to be allowed to be imported.
Inverter firmware and software is just one albeit obvious example for sure. This is again part of a broader supply chain security issue too. Dismissing the origin of manufacture is burying one’s head in the sand.
Baseless baiting, scaremongering and spreading disinformation. The real danger is at home with these politicians, not from China.
Does this senator think that China is going to take control of all of its exported electronic products in order to weaponise them against western countries?
If so, then shutting down solar PVs is hardly going to bring Australia to its knees.
These politicians meaning politicians as a class generally, or just politicians from the side of politics, or parties, you disagree with? Those are vastly different things. While I would certainly agree some Australian politicians are more dangerous than others, I suspect we’d differ as to exactly whom and why.
Those in power have the potential to be far more dangerous than the opposition. Those who pursue radical ideologies and agendas are far more dangerous than those who pursue mainstream or traditional positions. And those supported by the media have far greater potential to be dangerous than those rigorously criticised and condemned in print, on radio, and on TV, for every alleged act or statement they make that the media dislike.
Of course. Compromising smart devices is precisely what forms a botnet.
I personally agree with the Minister, we need to consider the risk associated with these devices
If it’s on Sky News you do have to analyse it for political point scoring because it’s basically a conservative mouthpiece which is what this article did. And the article made some good points about the things already in place that would make such an attack unsuccessful on a wide basis. Before you can backdoor something you need access which would involve breaking encryption which is almost impossible without human engineering.
We do probably need to upgrade our intelligence apparatus so they can properly analyse such threats and have plans in place if such an attack did take place but I put this one in the highly unlikely basket.
You do realise that the most logical place to backdoor something, or even push updates to it, is from the manufacturer? Who do you think writes the firmware? Who sends the updates?
I think it’s a bit tricky, on one hand these devices pose a significant risk, but that said. the alternatives are significantly more expensive. Worth the cost?
“However, the risk of a critical security vulnerability – such as an unsecured login to an inverter – isn’t dependent on a product’s country of manufacture. Any internet-exposed device with a vulnerability can be exploited by any attacker that finds it.”
This simply is not true. Of course it can be dependent on where it is manufactured.
Hi Ali, i partially agree, you can hack any device no matter where it is located. My concern is if it’s made in China, the Chinese Government could have the manufacturer install a deliberate vulnerability.
Inverters from places like Europe or the US are built to be tough. The Chinese inverters may be build the back door left wide open for hackers!
Forbes today published an article titled “Chinese Malware Could Cut Power To U.S. Military Bases, Businesses And Homes, Report Claims”. Look, I understand that we want to defend our choices (and egos) to buy low-cost products, but the risk is there. On the low end, it’s not much different from the denial of service attacks that happen every day with technology. But this has the potential to be much more widespread. Proactively managing the risk is key.
Hi Sridhar, I completely agree. In a price vs safety decision, we should probably pick safety. Especially for the military
Hi Bryce, not sure if you saw it, but the army has got rid of their Chinese made Drones for this reason. Perhaps it’s about time they get rid of any Chinese made solar inverters and PV cells.
I am really concerned about the risk these inverters pose. We’re meant to be installing millions of homes worth of panels in the coming years and we’re going to hook each of them up to a security risk
Since reading this, I’ve done a bit more of my own research. These inverters are really worrying, apparently Chinese Government policy dictates that they are allowed to take any data collected by a Chinese company, even if it is Australian data.
Hi Toby, This is correct, the Chinese Government imposes this on any chinese owned company, this could include the owners, or the contract manufacturers of various solar and PV products.
I would like this topic be updated in view of the alleged “secret” radio circuitry, that would bypass the grid and internet based issues covered in this article.
I proceeded with purchases after reading this, although I ended up selecting Enphase inverters, due to the risk potential. At the time I was looking to get a battery which coloured my decision, but found them all too expensive. With the Federal battery rebate I am reassessing, but this new potential of risk is worrying.
I would expect that the government might investigate the claims themselves. This should not take too long, or be impossible to mitigate the risk. But this needs to be addressed now, before the great influx of installations take place.